If encryption is altogether a new concept for you, check out our last post on the basics of encryption. In this post, we will be branching out into a different category, known as file-level encryption.
When trying to source the meaning of file-level encryption, a plethora of related words can oftentimes be overwhelming. For example, file encryption, file/folder encryption, file-level encryption, encrypting file system, filesystem-level encryption, volume encryption, partition encryption, storage encryption, hardware-based encryption, full disk encryption, etc. You get the point. Out of all the jargons and terminologies, what truly defines file-level encryption the best?
While these set of words might seem related, when delved deeper, the concept becomes more confusing. And trying to glean an all-rounded definition seems impossible.
What is File-level Encryption?
Nowadays, a file is no longer limited to its physical form but can also appear in digitized format. And encryption is applied to secure those files. Though the concept might seem easy to grasp, in reality, the process of file encryption is in fact, a rather complex one to execute.
File management, simply put, is the process of organizing data in a hierarchical process and managed by using catalogs, which makes storing and retrieving a lot easier. The operation on the file largely takes place in three areas and are administered using different methods (namely the physical storage devices, the operating system kernel, and the application). The encryption process is also different in accordance with the behavior of the three respective areas.
Categorizing the Different Methods
Among the three methods, let’s put aside the hardware-based disk encryption in the physical storage device. This method is about encrypting the entire hard disk, so if the actual hard disk is stolen, there is really no one or thing to technically blame. The market terms related to encryption that use “hardware based”, “full disk”, “whole disk”, “disk” fall under this category.
Next, let’s look at the two area in which file-level encryption is applicable. From the top, there is the User Space where applications run while the Kernel sits below this layer and is the central part of the operating system.
As shown in the diagram, the Kernel is separated into three different sections (Partition, Volume, and Filesystem). The disk drive (HDD) performs the input and output, all the way through the partitions and volumes of the top layer of the virtual drive, and lastly to the filesystem presented at the top layer. Encryption for each layer of the operating system level is referred to as “partition encryption”, “volume encryption” as well as “(filesystem-level) file encryption”. The purpose of the parentheses is to differentiate file-level encryption that can take place in both the application layer as well as the filesystem level.
The Different Kinds of File-Level Encryption
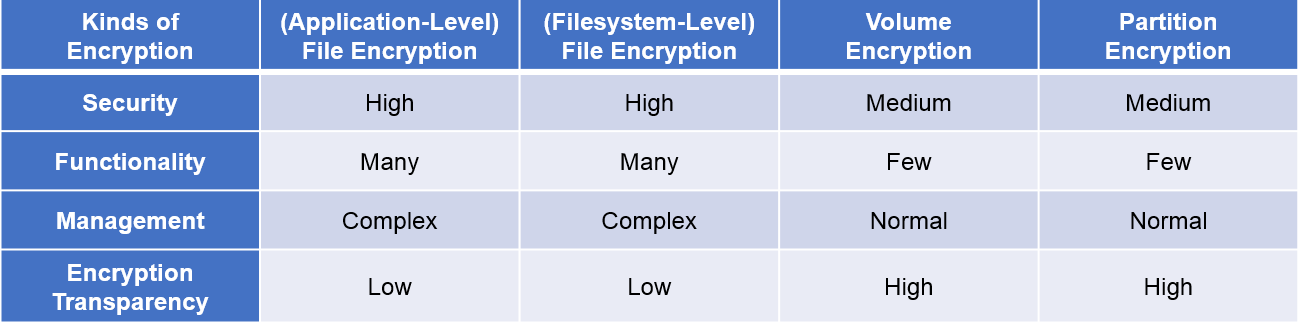
A good security tool can be measured by its user-friendliness as well as the ability to perform. The table below shows a simple comparison of the different kinds of file-level encryption in terms of ease of administration and level of security.
File encryption, be it at the application level of filesystem level, provides good security and high functionality. If the encryption is performed at the application level, key management and access control are both possible for file and folder. Although most file encryption provides authority management like access rights, log management, backup, and advanced interface environments, all these may pose a relatively large administrative burden on the system compared to other encryption methods. The overall administrative cost might increase too as each file or folder would entail complex procedures and detailed management. Therefore, when choosing a file encryption product, it is necessary to focus on several points including an intuitive user interface. A well-made user interface will not only reduce administrative costs but can also ease the burden on the management side, too.
Partition encryption and volume encryption both have relatively easy management control compared to that of file encryption. But at the expense of lower security. The inherently antagonistic relationship of sacrificing security for its ease of use can be seen here. On one hand, with higher security, management can get a bit uncomfortable; when there is the ease of management, safety is risked. Hence, other features are also important factors that should not be overlooked when choosing the right encryption method.
Choosing the best encryption method can be tricky. The aforementioned are various encryption methods that collectively fall under the file-level encryption. It is important to note that encryption is not only limited to the file-level, other methods of encryption are also available. If encrypting the whole file is not a priority and having a diverse selection in what to encrypt sounds appealing, it may be worth checking out the advantages of column-level encryption.