According to a report by Intel in 2015, among companies experiencing data breaches, internal actors (employees, contractors, and third-party suppliers) were responsible for 43% of data loss, half of which was intentional, and half accidental.
Apart from accidental incidents, there are intruders, malicious insiders, and financially motivated attackers that will try to exploit privileged accounts in order to gain access to sensitive application data. When it comes to the database, the powerful database administrator (DBA) role falls under the category of privileged users. Once the DBA account has been exploited, attackers would have access to the sensitive data of the database. Because of the extensive access given to such accounts, damage done by attackers using privileged accounts often is the hardest to detect and the most extensive.
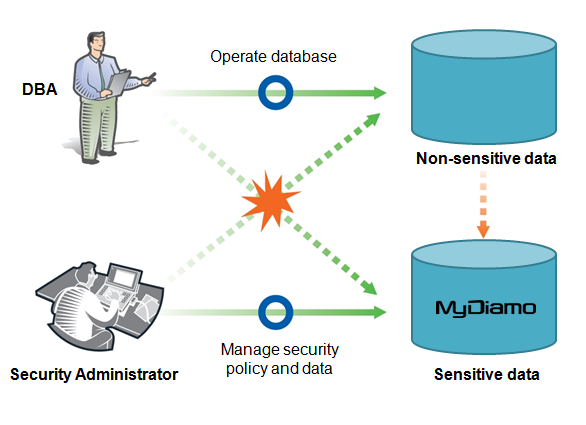
This is why having proper authority separation is crucial in order to mitigate the damage from internal harm. There is a strong need for proper security controls inside the database that differentiate the privileges of the DBA, and security administrator. This limits and only allows certain individuals with approved rights to access approved information.
As a comprehensive solution, MyDiamo not only provides encryption/decryption of information, but also allows for authority separation that separates the privileges of the people who access the database. The security administrator, for example, is able to set up security policies and manage the authorization of who can use the encryption and decryption keys. The security administrator can also limit the authority of a DB user including the DBA to specific columns only so they are unable to touch other columns. MyDiamo also allows the security administrator to see who has accessed which encrypted columns, and what changes they have made allowing for easy management. With these security policies in place, even when the DBA account has been compromised, attackers will not be able to access the sensitive data.
Ideally, the security administrator should define policies and procedures and monitor data encryption/decryption, while the DBA should be able to implement these controls with minimal impact on their main role: administering databases. Solutions that separate authorization from database administration simplify the separation of roles between security, IT operations and DBA, and provide for a stronger and secure database.
As long as the existence of important and valuable data prevails, there will always be illegal attempts in acquiring this data. As long as this relationship exists, we have no choice but to protect sensitive data. With encryption and proper authority separation, security can be enhanced. It becomes important to recognize that all harm is not always from the outside. Whether it be accidental or intentional, internal care must be given proper attention to.