In reality, having perfect web security is nigh impossible.
Even for the most skilled and specialized security expert, designing, maintaining, and operating the perfect security system is a high feat. This is because web security, in particular, has no standard security measures or methods, and secure environments are built accordingly to meet the particular situation. The types of security solutions are vast and diverse and are often difficult to find the ‘perfect’ fit.
For proper web security, corporate security administrators must first understand the IT system structure to apply web security to the system accordingly.
How is the IT System Structured?
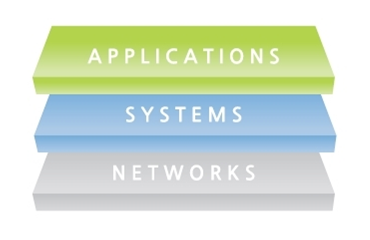
Generally, the IT system of a company is composed of three layers– the networks, systems, and applications layer. Various server system architectures generally follow this structure.
The networks layer that sits at the bottom is mostly in charge of communications relating to the transmission and reception of data. The systems layer above acts as a platform for the operating systems such as Windows and Linux to run multiple applications. And finally, the applications layer focuses on communication interfaces and end-user application services. This layer is seen as the most important layer to be protected. Reason being, hackers mainly attack the system through this layer, yet often than not, they don’t get enough security attention.
While establishing security for the network is simple and straightforward, most would find establishing security for the application layer confusing and daunting. To attain proper web security, it is crucial that all three layers of the IT system must be built securely, with special attention given to the application layer.
The Perfect Web Application Security
Just like building a house, a good foundation goes a long way. There are several factors that need to be emphasized to provide a strong sturdy base. In the same light, when setting up security at the application layer, all stages from the development to deployment, and maintenance need to be taken into account. Every single component is essential as it comes together to build a fully equipped and comprehensive web application security, like how maintenance crew, quality bricks, cement, thermal protection, etc. are necessities to build a house. A strong web application security requires secure coding, web scanner, web-based malware detection, web application firewall (WAF), and data security solution.
Secure Coding
Secure coding is the first basic necessity needed to build a secure web application server. During the development phase, it is imperative to write code as securely as possible in order to minimize future vulnerabilities exploitation.
According to Gartner, a leading technology research and advisory company stated that by reducing the possibility of vulnerability by 50%, security response costs can also be scaled down by 75%. Rather than a speedy deployment, a secure and systematic development counts for more.
Web Scanner
After a house has been built, maintenance comes into play. This is where a web scanner is needed to constantly inspect for possible vulnerabilities. Web scanner is often referred to as the “web vulnerability assessment tool”. It is a separate program applied alongside the web application to analyzes potential vulnerabilities. There are a variety of web scanners available with different performance results and operations, but its core objective remains the same—to periodically and constantly keep check of the application status.
Web Application Firewall (WAF)
The web scanner alone isn’t sufficient when it comes to protection. It may alert of a vulnerability, but won’t be able to fight against it. WAF, on the other hand, can act as a fence or wall around the house, preventing intruders from approaching and reducing the risks of undetected internal access.
A WAF serves to detect and respond to external web attacks or threats as well as protecting the security solution within the application from external invasion, including preventing malicious codes being uploaded onto the web server.
WAF does not have to be built within the server and can be conveniently installed separately. Unlike a typical firewall that utilizes blacklist and whitelist IP information, the latest web application firewall technology blocks a variety of real-time attacks by logically analyzing the threat characteristics.
Web-based Malware Detection
Let’s not forget the inside of the house would also require inspection – web-based malware detection and malware removal solution exists for that reason. Web-based malware detection exists to identify Web Shell, which is a form of malicious code that runs within the application. Hackers are able to bypass the security system and gain access without authentication through Web Shell. And the probability of malware infection in the system without WAF in place is naturally higher. If the system is already infected, malware removal solutions might be too late. Thus, like the web scanner, web-based Malware Detection is also a necessary component for periodic maintenance and checking.
Data Security
Every process will always require a final step — to protect all valuables such as cash, jewelry or even sensitive personal data. In a typical web application environment, a database is used to store and manage data. As such a proper data encryption solution is needed to securely manage the database. However, data encryption alone isn’t enough. Proper authority separation with access control and auditing is important as to determine who has access to what, and when it has been accessed. To top it off, include a good key management system (KMS) to manage those encryption keys.
With the application layer being equipped with the 5 components mentioned above, you can rest better knowing your system is well-protected. Though there is no guarantee there is a ‘perfect’ web application security. Constant vigilance can also help prevent unwanted web attacks.